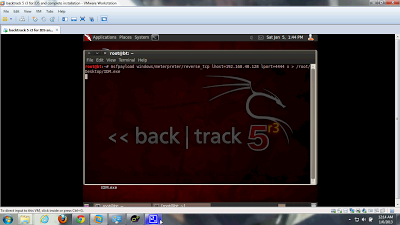
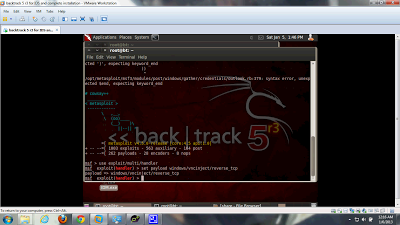
Basic commands of Backtrack
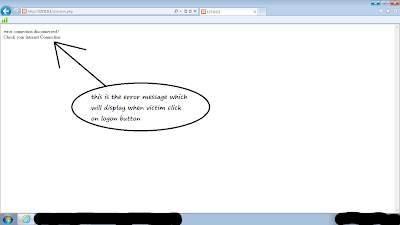
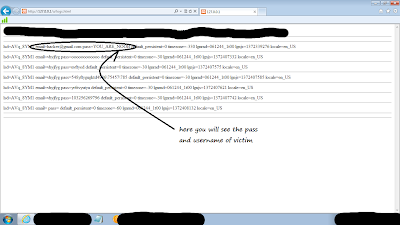
Click to enlarge image
Know about your System
uname Print System Information
who Show Who Is Logged On
cal Displays Calculator
date Print System Date And Time
df Report File System Disk Space Usage
du Estimate File Space Usage
ps Displays Information Of Current Active Processes
kill Allows To Kills Process
clear Clear The Terminal Screen
cat /proc/cpuinfo Cpuinfo Display CPU Information
cat /proc/meminfo Display Memory Information
File operator
pwd Print Name Of Current/Working Directory
cd Changing The Working Directory
cp Copy Files Or Directory
rm Remove Files And Directory
ls List Of Directory Contents
mkdir Make Directory
cat Concatenate Files And Print On Standard Output mv Move Files
chmod Change Files Permissions
Network
ifconfig To Config Network Interface
ping Check The Other System Are Reachable From The Host System
wget Download Files From Network
ssh Remote Login Program
ftp Download/Upload Files From/To Remote System
last Displays List Of Last Logged In User
telnet Used To Communicate With Another Host Using THe Telnet Protocol
Compression
tar To Store And Extract Files From An Archive File Known As Tar File
gzip Compress Or Decompress Named Files
Searching Files